Maximum control over digital identities: Secure your data reliably with SysEleven IAM
With SysEleven IAM, you get complete control over digital identities. Authorized users can securely access critical resources, which makes sure that your data is protected reliably and efficiently.

Efficient access management: IAM for your cloud environment
Manage access rights centrally and securely to ensure the integrity and confidentiality of your IT environment. By using our integrated IAM solution, you can efficiently control user access, securely manage the identities of your employees and systems, and meet tough compliance requirements. Whether for small teams or large enterprises, our solution adapts to your individual needs and protects your sensitive data and critical systems from unauthorized access.
Centralized, easy management
With IAM, you can effortlessly track all user accounts and access rights and manage them easily and efficiently.

Compliance made easy
With our GDPR-compliant IAM hosting in German ISO-27001 certified data centers, you can easily meet all legal data protection requirements.

Companies that already trust us



















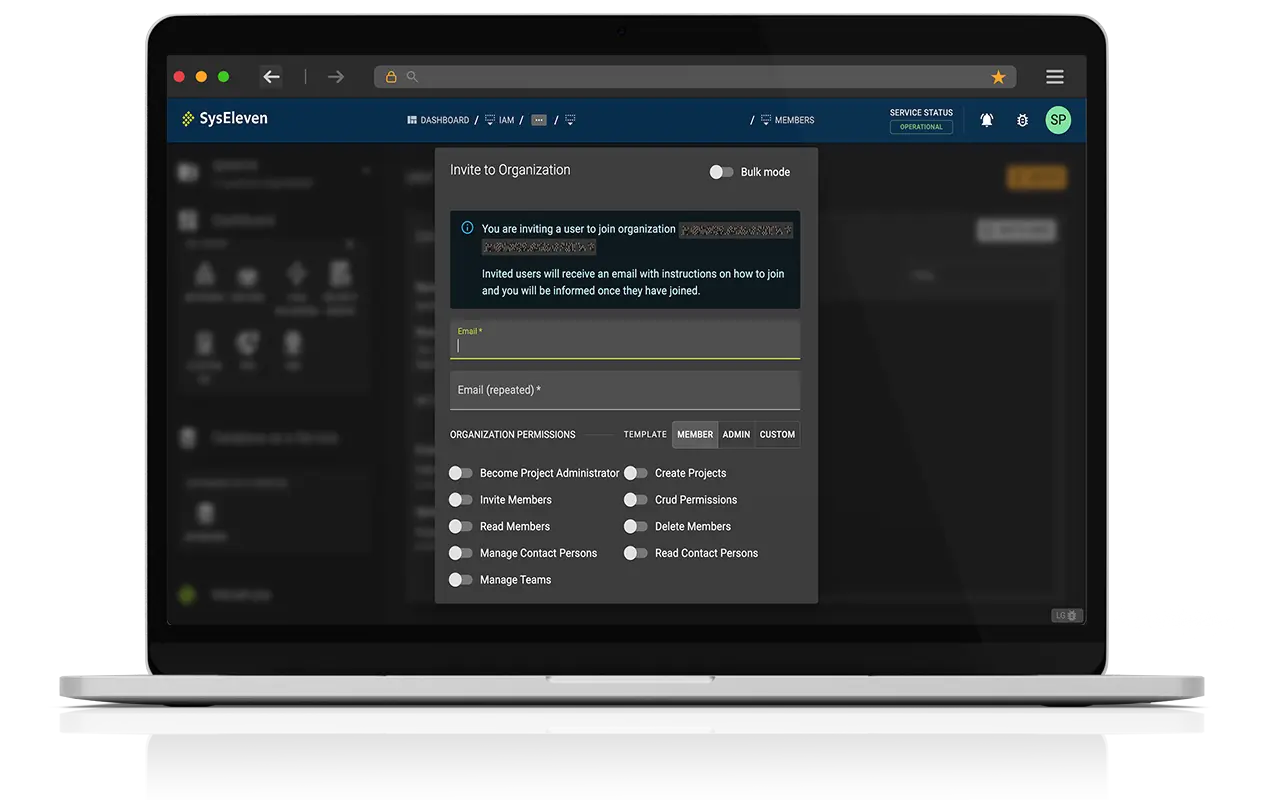
User management
A user exists only once on the SysEleven platform with a unique identifier. Access to resources within an organization is controlled solely through finely tuned permissions.
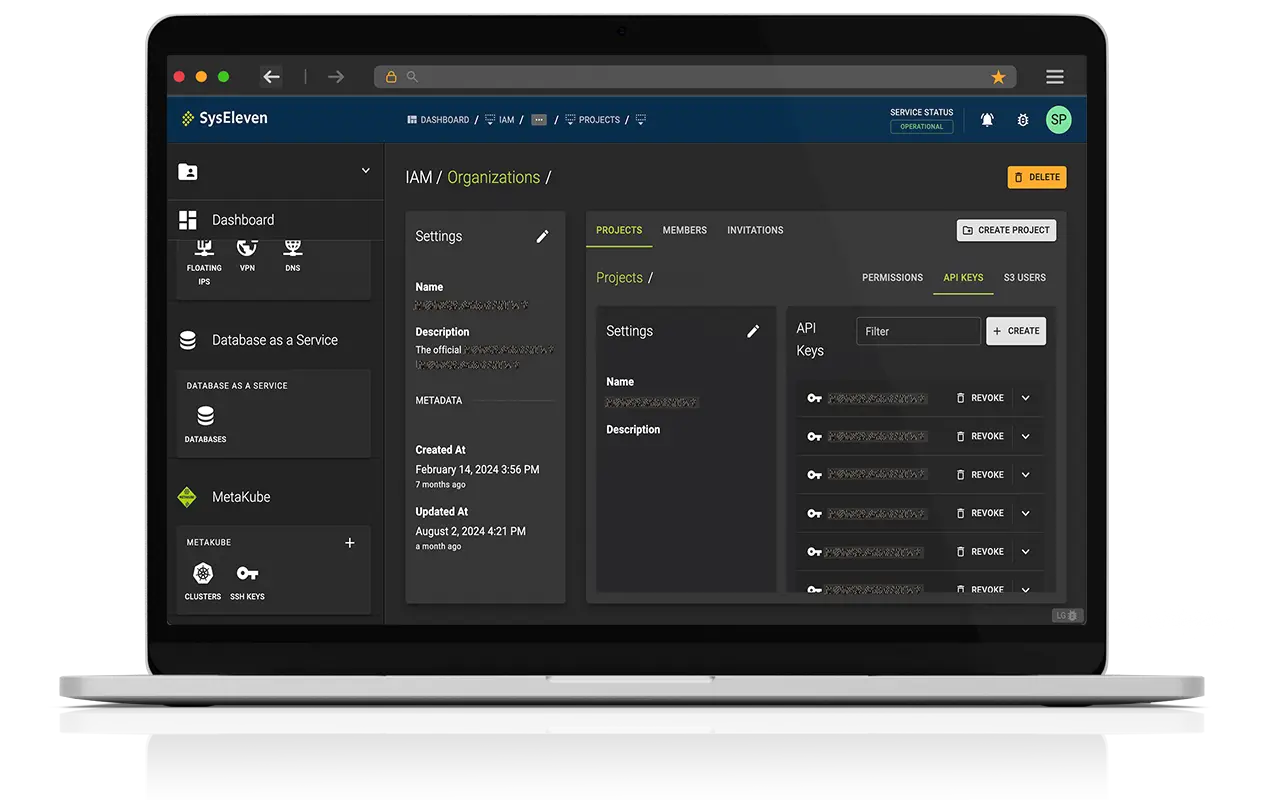
API keys
Users can create project-specific API keys, which can then be used for authentication with the SysEleven Cloud API. These keys are limited to a specific project and can be revoked anytime.
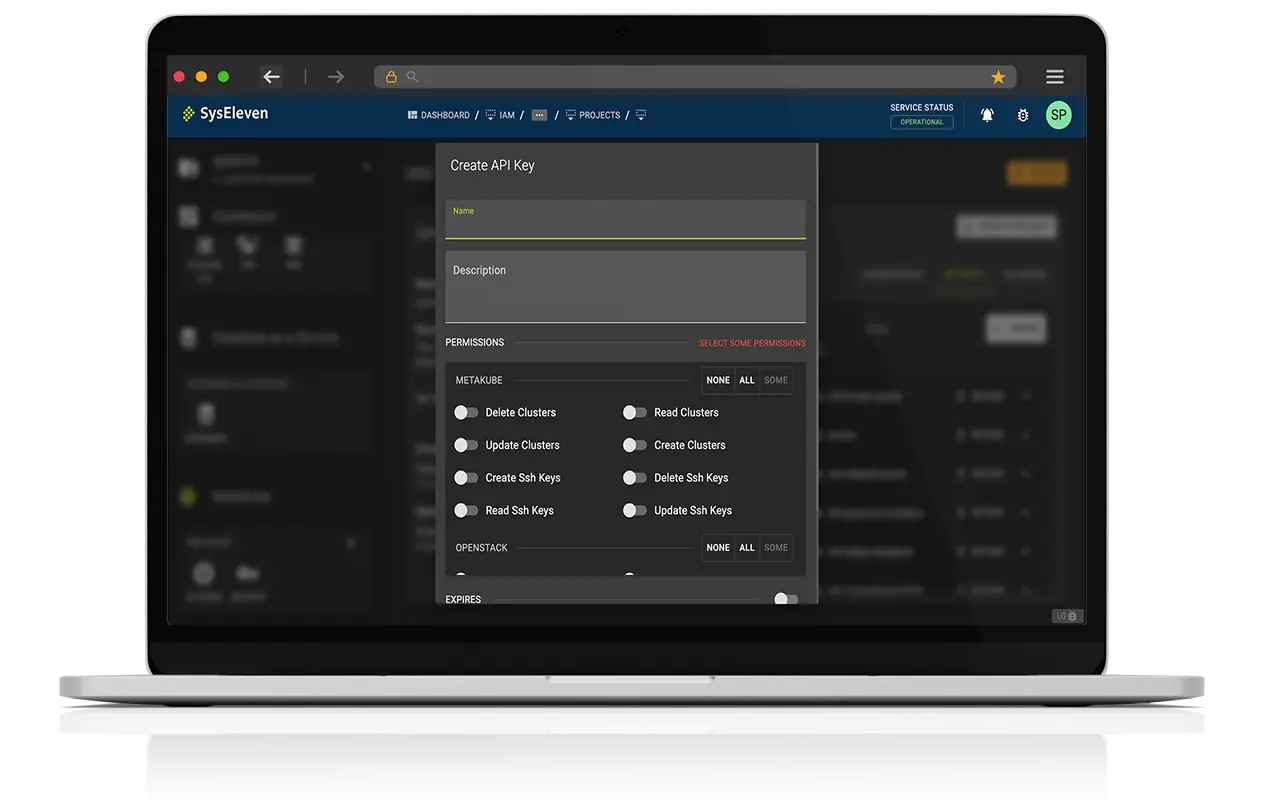
Service accounts
Service accounts are an evolution of SysEleven’s API keys. They provide easier access to the SysEleven OpenStack Cloud and greater flexibility for software to interact with it.
Relationship-based access control (RBAC)
We use advanced ReBAC technology to set permissions flexibly and precisely based on user-resource relationships. Supported by OpenFGA, it offers a modern solution perfectly tailored to the demands of your dynamic cloud environments.
Use cases

Protecting sensitive health data: Secure access to patient records
By using IAM, you make sure that only authorized medical personnel have access to patient records and health data. Precise permission assignments and comprehensive authentication measures safeguard the confidentiality and integrity of sensitive medical information while meeting tough healthcare data protection regulations.

Protection and integrity: How IAM secures financial data and transactions
Banks and financial institutions use IAM to manage user accounts, transfers, and transactions. IAM protects against unauthorized access and fraud by ensuring that all economic activities are secure and transparent. Detailed logging and monitoring of transactions maintain the integrity of bank data while ensuring compliance with regulatory requirements.
Pricing
The complete price list can be requested at sales@syseleven.de
FAQs
IAM is based on identities, permissions, and policies:
- Identities: Every user or entity that wants to access resources has a unique digital identity, such as a username, e-mail address, or other identifier.
- Permissions: Each identity has specific permissions that define which resources or services they can access. Permissions can be highly granular, ranging from “read” to “write” and “delete.”
- Policies: IAM uses policies to determine which identities can access which resources and what actions they can perform. These policies are rules that are created and managed by administrators.
- Authentication & authorization: When a user logs in (authentication), the IAM system verifies their identity and then checks the assigned permissions and policies to decide whether access is granted or denied (authorization).
Integrating IAM into your existing cloud environment offers numerous benefits:
- Centralized management: You can control all user accounts and access rights in one place, which simplifies management and ensures consistency.
- Enhanced security: IAM protects your cloud resources from unauthorized access with precise access control and features like multi-factor authentication (MFA).
- Scalability: IAM can flexibly adapt to the growing demands of your cloud environment, which allows you to integrate new users and applications easily.
- Cost and time savings: Automation of access processes reduces administrative effort and minimizes errors, which saves time and reduces operational costs.
- Compliance and reporting: IAM helps you to comply with security and data protection regulations with detailed logs and reports on access activities.
IAM ensures compliance with data protection regulations like GDPR through several key features:
- Access control: Through precise role and permission management, IAM makes sure that only authorized personnel have access to personal data, which supports the principle of data minimization.
- Transparency and traceability: IAM provides detailed logs and reports on access and activity data. This is essential for audits and compliance verification.
- Secure authentication: With multi-factor authentication (MFA) features, IAM protects user identities and prevents unauthorized access to sensitive data.
- Privacy by design: IAM systems can be configured to integrate privacy principles right from the start, such as implementing privacy policies and automated permission checks.
- Rights management: IAM enables precise access rights management, which ensures that access requests and changes are transparent and documented, thus meeting GDPR requirements for data processing and security.



